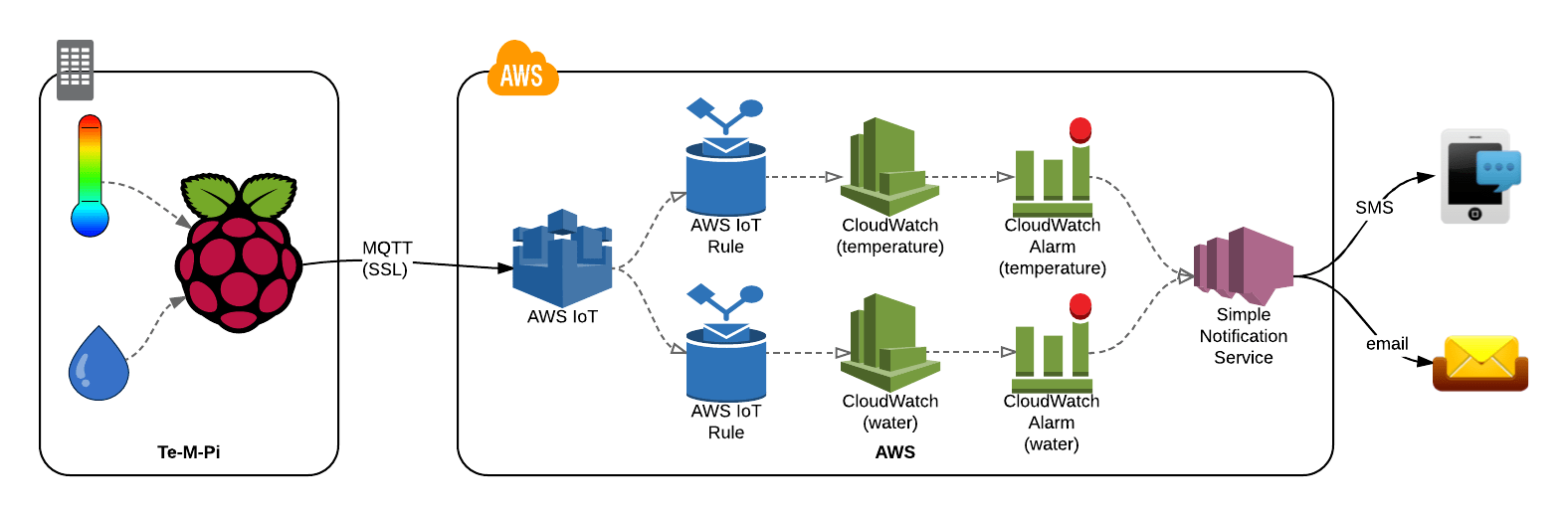
To securely connect a remote Raspberry Pi to an AWS VPC over the internet, you can use a combination of AWS IoT, VPC, and AWS VPN services. This allows you to establish a secure and private connection between your Raspberry Pi and the AWS cloud, enabling you to securely send and receive data, manage devices, and perform other IoT operations.
Here are some of the benefits of using this approach:
- Security: This approach provides a secure connection between your Raspberry Pi and the AWS cloud, protecting your data from unauthorized access.
- Scalability: You can easily scale your IoT solution to accommodate a growing number of devices.
- Reliability: The AWS cloud is a reliable and scalable platform, ensuring that your IoT solution will be up and running when you need it.
To get started, you will need to create an AWS account and set up an AWS VPC. You will also need to install the AWS IoT Device SDK on your Raspberry Pi. Once you have done this, you can follow the AWS documentation to configure your Raspberry Pi to connect to your AWS VPC.
Read also:Understanding The Profound Kumbaya Meaning A Journey Through History And Culture
Securely Connect Remote IoT VPC Raspberry Pi AWS Example
Connecting Raspberry Pi devices to AWS IoT securely over a Virtual Private Cloud (VPC) is a crucial aspect of IoT deployments. Here are 8 key aspects to consider:
- Authentication: Establish secure device identity.
- Authorization: Control access to AWS resources.
- Encryption: Protect data in transit and at rest.
- Network Segmentation: Isolate IoT devices from other network traffic.
- Identity Management: Manage and monitor device identities.
- Data Security: Protect sensitive data collected from devices.
- Compliance: Adhere to industry regulations and standards.
- Scalability: Support a growing number of connected devices.
These aspects work together to provide a secure and scalable IoT solution. For example, authentication ensures that only authorized devices can connect to the AWS IoT platform, while encryption protects data from eavesdropping. Network segmentation isolates IoT devices from other network traffic, reducing the risk of security breaches. Identity management allows you to track and manage all connected devices, while data security measures protect sensitive data collected from devices. Compliance ensures that your IoT solution meets industry regulations and standards, and scalability allows you to support a growing number of connected devices without compromising security.
1. Authentication
In the context of securely connecting remote IoT devices to AWS VPC over the internet, authentication plays a critical role in establishing a secure device identity. It ensures that only authorized devices can connect to the AWS IoT platform and access AWS resources. Without proper authentication, unauthorized devices could gain access to the network and compromise the security of the entire system.
There are several methods for authenticating IoT devices, including:
- X.509 certificates: Each device is issued a unique certificate that identifies it to the AWS IoT platform.
- JWT tokens: A JSON Web Token (JWT) is a compact, self-contained token that contains claims about the identity of the device.
- Custom authentication mechanisms: You can develop your own custom authentication mechanism that meets the specific needs of your application.
Once a device is authenticated, it is granted access to the AWS IoT platform and can begin sending and receiving data. Authentication is an essential component of a secure IoT system, as it helps to protect against unauthorized access and data breaches.
Here are some real-life examples of how authentication is used to securely connect remote IoT devices to AWS VPC:
Read also:The Alluring Story Of Kaoru Kuroki A Pioneering Icon In Japanese Entertainment
- A manufacturing company uses AWS IoT to connect thousands of sensors to the cloud. Each sensor is authenticated using a unique X.509 certificate, which ensures that only authorized devices can send data to the AWS IoT platform.
- A smart city uses AWS IoT to connect traffic lights, parking meters, and other devices to the cloud. Each device is authenticated using a JWT token, which is generated by a trusted third party. This ensures that only authorized devices can access the AWS IoT platform and send data.
By understanding the importance of authentication in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system.
2. Authorization
In the context of securely connecting remote IoT devices to AWS VPC over the internet, authorization is the process of controlling access to AWS resources. This is important because it ensures that only authorized devices and users can access the resources they need, while preventing unauthorized access to sensitive data and systems.
AWS provides a number of mechanisms for authorizing access to its resources, including:
- IAM policies: IAM policies allow you to control who can access AWS resources and what actions they can perform.
- Resource-based policies: Resource-based policies allow you to control access to specific AWS resources, such as S3 buckets or DynamoDB tables.
- Cognito identity pools: Cognito identity pools allow you to manage the identities of users who access your AWS resources.
When you are designing an IoT system, it is important to consider how you will authorize access to AWS resources. You should create IAM policies that grant the necessary permissions to your IoT devices and users, while denying access to unauthorized users.
Here are some real-life examples of how authorization is used to securely connect remote IoT devices to AWS VPC:
- A manufacturing company uses AWS IoT to connect thousands of sensors to the cloud. Each sensor is authorized to send data to a specific S3 bucket. The IAM policy for the S3 bucket only allows authorized users to access the data.
- A smart city uses AWS IoT to connect traffic lights, parking meters, and other devices to the cloud. Each device is authorized to access specific AWS services, such as Amazon DynamoDB and Amazon Kinesis. The IAM policies for these services only allow authorized users to access the data.
By understanding the importance of authorization in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system.
3. Encryption
Encryption is a crucial component of securely connecting remote IoT devices to AWS VPC over the internet. It ensures that data is protected from unauthorized access, both while it is being transmitted over the network and while it is stored at rest. Without encryption, data could be intercepted and compromised by unauthorized users.
AWS provides a number of mechanisms for encrypting data, including:
- TLS/SSL encryption: TLS/SSL encryption is used to encrypt data in transit between devices and AWS services.
- Encryption at rest: Encryption at rest is used to encrypt data that is stored in AWS services, such as S3 buckets and DynamoDB tables.
When you are designing an IoT system, it is important to consider how you will encrypt data in transit and at rest. You should use TLS/SSL encryption to protect data that is being transmitted over the network, and you should use encryption at rest to protect data that is stored in AWS services.
Here are some real-life examples of how encryption is used to securely connect remote IoT devices to AWS VPC:
- A manufacturing company uses AWS IoT to connect thousands of sensors to the cloud. All data that is transmitted between the sensors and AWS services is encrypted using TLS/SSL encryption. Additionally, all data that is stored in AWS services is encrypted at rest using AES-256 encryption.
- A smart city uses AWS IoT to connect traffic lights, parking meters, and other devices to the cloud. All data that is transmitted between the devices and AWS services is encrypted using TLS/SSL encryption. Additionally, all data that is stored in AWS services is encrypted at rest using AES-256 encryption.
By understanding the importance of encryption in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system.
4. Network Segmentation
In the context of securely connecting remote IoT devices to AWS VPC over the internet, network segmentation plays a vital role in isolating IoT devices from other network traffic. This is important because it reduces the risk of security breaches and data leaks. Without network segmentation, IoT devices could be compromised by attackers who gain access to the same network segment.
- Virtual Private Clouds (VPCs)
VPCs allow you to create isolated network segments within the AWS cloud. You can then place your IoT devices in a VPC to isolate them from other network traffic. VPCs provide a secure and scalable way to connect your IoT devices to AWS services. - Security Groups
Security groups act as firewalls that control the inbound and outbound traffic of your IoT devices. You can use security groups to restrict access to your IoT devices to only the necessary ports and IP addresses. This helps to protect your IoT devices from unauthorized access. - Network Access Control Lists (NACLs)
NACLs are similar to security groups, but they apply to subnets within a VPC. You can use NACLs to control the traffic that is allowed to enter and leave a subnet. This provides an additional layer of security for your IoT devices. - PrivateLink
AWS PrivateLink allows you to create private connections between your IoT devices and AWS services. This means that your IoT devices can communicate with AWS services without having to traverse the public internet. PrivateLink provides a more secure and reliable way to connect your IoT devices to AWS services.
By understanding the importance of network segmentation in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system.
5. Identity Management
Identity management is a critical component of securely connecting remote IoT devices to AWS VPC over the internet. It allows you to manage and monitor the identities of your IoT devices, ensuring that only authorized devices can connect to your network and access your resources.
Without proper identity management, it would be difficult to track and manage the growing number of IoT devices that are being deployed. You would also be at risk of unauthorized devices gaining access to your network and compromising your data.
AWS provides a number of tools and services that can help you to manage and monitor the identities of your IoT devices. These include:
- AWS IoT Device Registry: The AWS IoT Device Registry allows you to create and manage the identities of your IoT devices. You can use the Device Registry to track the status of your devices, view their certificates, and manage their access to AWS resources.
- AWS IoT Device Shadow: AWS IoT Device Shadow allows you to create a virtual representation of your IoT devices in the cloud. You can use Device Shadow to store and retrieve device state information, and to control your devices remotely.
- AWS IoT Device Defender: AWS IoT Device Defender is a managed service that helps you to secure your IoT devices. Device Defender can monitor your devices for suspicious activity, and it can automatically take action to protect your devices from threats.
By understanding the importance of identity management in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system.
6. Data Security
In the context of securely connecting remote IoT devices to AWS VPC over the internet, data security is of paramount importance. IoT devices collect and transmit vast amounts of sensitive data, such as customer information, financial data, and trade secrets. This data must be protected from unauthorized access, both while it is being transmitted over the network and while it is stored in the cloud.
AWS provides a number of tools and services that can help you to protect the data collected from your IoT devices. These include:
- Encryption: Encryption is used to protect data from unauthorized access, both while it is being transmitted over the network and while it is stored at rest. AWS provides a number of encryption options, including TLS/SSL encryption, encryption at rest, and KMS encryption.
- Access control: Access control is used to restrict access to data to only authorized users. AWS provides a number of access control mechanisms, including IAM policies, resource-based policies, and Cognito identity pools.
- Data monitoring: Data monitoring is used to detect and respond to security threats. AWS provides a number of data monitoring tools and services, including CloudTrail, GuardDuty, and Security Hub.
By understanding the importance of data security in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system. Here are some real-life examples of how data security is used to protect sensitive data collected from IoT devices:
- A manufacturing company uses AWS IoT to collect data from thousands of sensors on its production line. This data is used to improve the efficiency of the production line and to identify potential problems. The company uses encryption, access control, and data monitoring to protect the sensitive data collected from its sensors.
- A smart city uses AWS IoT to collect data from traffic lights, parking meters, and other devices. This data is used to improve the flow of traffic and to make the city more efficient. The city uses encryption, access control, and data monitoring to protect the sensitive data collected from its devices.
These examples illustrate the importance of data security in securely connecting remote IoT devices to AWS VPC. By understanding the importance of data security, you can develop a more secure and robust IoT system.
7. Compliance
In the context of securely connecting remote IoT devices to AWS VPC over the internet, compliance plays a crucial role in ensuring that your IoT system meets the requirements of industry regulations and standards.
- Data Protection Regulations
There are a number of data protection regulations that apply to IoT devices, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States. These regulations impose specific requirements on how personal data is collected, used, and stored. By understanding these regulations and implementing the necessary controls, you can ensure that your IoT system is compliant. - Industry Standards
There are also a number of industry standards that apply to IoT devices, such as the ISO/IEC 27001:2013 standard for information security management. These standards provide guidance on how to implement security controls to protect IoT devices and data. By adhering to these standards, you can demonstrate that your IoT system is secure and compliant.
By understanding the importance of compliance in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system. Here are some real-life examples of how compliance is used to protect sensitive data collected from IoT devices:
- A healthcare company uses AWS IoT to collect data from medical devices implanted in patients. This data is used to monitor the patients' health and to provide remote care. The company has implemented a number of security controls to protect the sensitive data collected from these devices, including encryption, access control, and data monitoring. The company has also obtained certification to ISO/IEC 27001:2013, demonstrating its commitment to data security and compliance.
- A financial services company uses AWS IoT to collect data from ATMs and other financial devices. This data is used to prevent fraud and to improve the customer experience. The company has implemented a number of security controls to protect the sensitive data collected from these devices, including encryption, access control, and data monitoring. The company has also obtained certification to ISO/IEC 27001:2013, demonstrating its commitment to data security and compliance.
These examples illustrate the importance of compliance in securely connecting remote IoT devices to AWS VPC. By understanding the importance of compliance, you can develop a more secure and robust IoT system.
8. Scalability
In the context of securely connecting remote IoT devices to AWS VPC over the internet, scalability is of paramount importance. As the number of IoT devices deployed in the field grows, it is essential to have a system that can support this growth without compromising security.
- Flexible and elastic infrastructure
AWS provides a flexible and elastic cloud infrastructure that can scale to meet the demands of a growing number of IoT devices. You can easily add or remove devices from your system as needed, and AWS will automatically provision the necessary resources to support them. - Lightweight and efficient protocols
AWS IoT supports lightweight and efficient protocols, such as MQTT and LoRaWAN, which are designed to minimize the bandwidth and processing power required by IoT devices. This makes it possible to connect a large number of devices to your system without overwhelming your network. - Managed services
AWS provides a number of managed services that can help you to scale your IoT system, including AWS IoT Device Management and AWS IoT Device Defender. These services can automate many of the tasks involved in managing a large number of IoT devices, such as provisioning, updating, and monitoring.
By understanding the importance of scalability in securely connecting remote IoT devices to AWS VPC, you can develop a more secure and robust IoT system. Here are some real-life examples of how scalability is used to support a growing number of connected devices:
- A manufacturing company uses AWS IoT to connect thousands of sensors to the cloud. The company is using AWS IoT to monitor its production line and to identify potential problems. The company has been able to scale its IoT system to support the growing number of sensors that it is deploying.
- A smart city uses AWS IoT to connect traffic lights, parking meters, and other devices to the cloud. The city is using AWS IoT to improve the flow of traffic and to make the city more efficient. The city has been able to scale its IoT system to support the growing number of devices that it is deploying.
These examples illustrate the importance of scalability in securely connecting remote IoT devices to AWS VPC. By understanding the importance of scalability, you can develop a more secure and robust IoT system.
FAQs on Securely Connecting Remote IoT VPC Raspberry Pi AWS
This section addresses frequently asked questions and misconceptions regarding the secure connection of remote IoT devices to AWS VPC via Raspberry Pi.
Question 1: What are the primary benefits of using this approach?
Answer: This approach offers several advantages, including enhanced security, scalability, and reliability. It allows for secure data transmission, efficient device management, and seamless integration with AWS cloud services.
Question 2: What measures are in place to ensure secure data transmission?
Answer: Data security is a top priority. Encryption techniques, such as TLS/SSL encryption and encryption at rest, are employed to protect data during transmission and storage. Additionally, access control mechanisms restrict data access to authorized personnel only.
Question 3: How does this approach address scalability concerns?
Answer: The AWS cloud infrastructure is designed to be flexible and scalable, enabling seamless accommodation of a growing number of connected devices. AWS IoT supports lightweight protocols to minimize bandwidth and processing requirements, facilitating the connection of numerous devices without overwhelming the network.
Question 4: What are the key considerations for network security?
Answer: Network segmentation plays a crucial role in isolating IoT devices from other network traffic, reducing the risk of security breaches. Virtual Private Clouds (VPCs), security groups, and Network Access Control Lists (NACLs) are utilized to establish secure network boundaries.
Question 5: How is device identity managed and monitored?
Answer: Identity management is essential for controlling device access and ensuring authenticity. AWS IoT Device Registry, AWS IoT Device Shadow, and AWS IoT Device Defender work together to create a virtual representation of devices, track their status, and provide remote control capabilities.
Question 6: What compliance measures are in place to meet regulatory requirements?
Answer: Compliance with industry regulations and standards is a priority. This approach adheres to data protection regulations like GDPR and CCPA, as well as industry standards such as ISO/IEC 27001:2013. By meeting compliance requirements, organizations can demonstrate their commitment to data security and privacy protection.
This FAQ section aims to clarify common concerns and provide valuable insights into the secure connection of remote IoT devices to AWS VPC via Raspberry Pi.
For further exploration, refer to the following article sections:
- Importance and Benefits
- Key Considerations
- Step-by-Step Guide
- Best Practices
Securely Connect Remote IoT VPC Raspberry Pi AWS
To strengthen the security of your remote IoT devices connected to AWS VPC via Raspberry Pi, consider implementing the following tips:
Tip 1: Implement Strong Authentication and Authorization:Utilize robust authentication mechanisms like X.509 certificates or JWT tokens to verify device identities and control access to AWS resources. Implement fine-grained authorization policies to restrict device actions and data access.
Tip 2: Encrypt Data Transmission and Storage:Employ encryption techniques such as TLS/SSL encryption and encryption at rest to protect data during transmission and storage. Ensure that sensitive data, like device credentials and sensor readings, is encrypted to prevent unauthorized access.
Tip 3: Segment and Isolate Network Traffic:Implement network segmentation using Virtual Private Clouds (VPCs), security groups, and Network Access Control Lists (NACLs) to isolate IoT devices from other network traffic. Restrict communication between devices and external networks only to what is absolutely necessary.
Tip 4: Manage and Monitor Device Identities:Utilize services like AWS IoT Device Registry and AWS IoT Device Shadow to create a virtual representation of devices, track their status, and remotely control their configurations. Monitor device activity for any suspicious behavior or unauthorized access attempts.
Tip 5: Adhere to Industry Standards and Regulations:Ensure compliance with relevant industry standards like ISO/IEC 27001:2013 and data protection regulations like GDPR and CCPA. Implement necessary security controls and regularly audit your system to maintain compliance and protect sensitive data.
By incorporating these tips into your IoT system design, you can significantly enhance the security of your remote IoT devices connected to AWS VPC via Raspberry Pi, mitigating potential risks and ensuring the integrity of your data and devices.
Conclusion
In this article, we have explored the intricacies of securely connecting remote IoT devices to AWS VPC over the internet, using Raspberry Pi as an example. We have highlighted the key considerations, benefits, and best practices involved in establishing a secure and reliable connection.
By implementing the measures outlined in this article, you can protect your IoT devices from unauthorized access, data breaches, and other security threats. Securely connecting your IoT devices is essential for ensuring the integrity and privacy of the data they collect and transmit, enabling you to fully leverage the potential of IoT technology for your business or organization.
As the IoT landscape continues to evolve, it is imperative to stay abreast of the latest security best practices and advancements. By incorporating these into your IoT deployments, you can ensure that your devices remain secure and your data remains protected.